How DNS cache poisoning works
Users of MyEtherWallet, a web app for storing and sending ether and ethereum-based tokens, experienced an DNS hijacking attack that saw users of the service lose around $152k worth of ether -coindesk(24th April, 2018)
 |
As a result of the cache poisoning, multiple users were deceived into giving up their key to the wallet before transffering their cryptocurrencies into another digital wallet associated with the hackers. The threat of DNS cache poisoning lead to the loss of $152k worth of cryptocurrencies. And this is just a bit. DNS attack could be take comparatively less effort to make an attack and results in much bigger consequences.
So from this article, I'd like to talk about DNS cache poisoning
what is DNS attack?
Known as DNS spoofing, DNS cache poisoning, DNS amplification and DNS hijacking, is a type of exploit vulnerabilities in the DNS to divert internet traffic away from legitimate servers into fake ones.
If the attacker is in the same internal network with victim(not always this case) and able to send response more quick to this victim's DNS query than original DNS, then changes are higher for victims to get lead to fake ass websites which is usually a malicious phishing website where victims can be manipulated into downloading malware or submitting login or financial details.
How DNS resolution process works
1️⃣User types "www.google.com" into a web browser, which in turn creates a DNS query and sends it to the default DNS recursive Resolver server (Firstly, your pc will look over for the cache data and if there's no IP in it then Secondly, it will go over to /etc/hosts files for the mapping info. If there're still not a proper IP info then it will send to default DNS query)
2️⃣The DNS Recursive resolver is the first stop for the DNS query. In most cases it is a server hosted by the ISP
3️⃣After receiving a DNS query from a host computer's web browser, the DNS resolver will send a request to a DNS root server(There're only 13 original Root Server in the World expect for the mirror server - 10 in USA, 1 in Japan, 1 in Netherlands, and last one in Norway)
4️⃣The DNS root server responds to the DNS resolver with the address of a DNS top level domain(TLD) server that stores information (root server -> TLD(.com .edu .org .mil etc))
5️⃣The DNS resolver makes a request to the .com DNS TLD server
6️⃣The DNS TLD server responds with the IP address of an DNS Authoritative name server
7️⃣The DNS Resolver sends a query to the DNS Authoritative Name server
8️⃣The DNS authoritative name server holds the actual DNS IP records, and sends the IP address for "google.com" to the DNS Resolver
9️⃣The DNS Resolver sends to host computer a DNS response that contains the IP address of the website initially requested
🔟The user's web browser uses the IP address received from the DNS response to start a transport layer sercurity(TLS) encrypted connection session with google's web server.
Server responds and secure connection over port 443(https) is established. The web server begins transmitting thousands of packets of data containing web page resources
Server responds and secure connection over port 443(https) is established. The web server begins transmitting thousands of packets of data containing web page resources
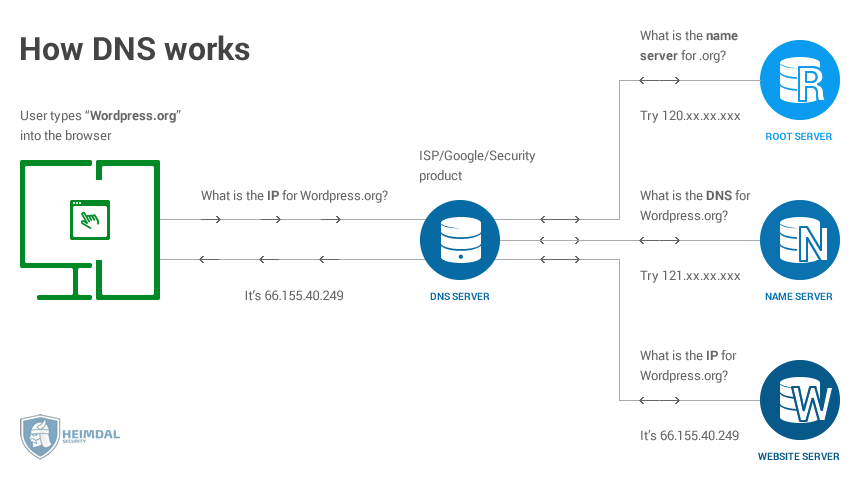 |
| First resolver server will reach to ROOT Server, next is TLD server, the last is Authoritative name server which has the actual IP record |
However, your pc doesn't send DNS query every single time you browse to certain website
Like I stated previously, it's much faster to have a local copy of the DNS phone book! Each OS windows and MAC by default, and UNIX via a Daemon stores a temporary DNS cache db that contains a list of all recently accessed domain names and the addresses that DNS calculated for them the first time a request was made.
In a local DNS cache entry, the "A" record contains the IPv4 address for the given website name. IPv6 addresses use the "AAAA" record. The DNS cache stores this address, the requested website name, and several other parameters from the host DNS entry.
So, How does the poisoning of DNS cache occur?
The corruption of DNS cache can be achieved by Network attacks that insert invalid DNS entries into the cache or computer malware.
Attackers have devised a way to spoof DNS responses to forge DNS reponses that look as if they are coming from legit DNS servers. If an atacker successfully spoofs a DNS response, it can make the receiving DNS server cache a poisoned record.
By being redirected to a wrong destination, people can end up suffering from phishing attack which is the ultimate goal of this type of MITMA(man-in-the-middle-attack)
Attacker can make their research for the victim previously, for example which website that victims tend to visit the most, what's the next website they mostly redirected to, etc.
Attacker could utilize any spoofing tool to spoof your DNS. I can think of one which is Ettercap. Ettercap is comprehensive suite for MITMA and it is a free, open source network security tool.
First attacker will make their fake HTML web-page which is the phishing one. Set it up on a Apache web server hosted on the attacker's computer.
They will scan the hosts in LAN and set the target computer, add to the target 1 and also select the IP address of the default gateway and add it to target2.
After they finished setting their targets, go and select dns_spoof from the plugins.
The plugin activates the process of bombarding the target machine with fake DNS reponses that resolve google.com(for example) to attacker's IP address where attacker already set up the new server to redirect.
From the redirected web server, attacker can designed the web server to get victim's credentials, financial infos, or lead victims to download malwares or they could insert scripts to go with another application attack such as XSS.
OF COURSE
There is "Transaction ID" where the DNS queries and responses
contain by the application layer of the user's computer.
However, the Transaction ID is only 16 bits and DNS servers accept almost simultaneous responses to requests. That would allow attackers to make multiple guesses about the transaction ID as a form of brute force attack.
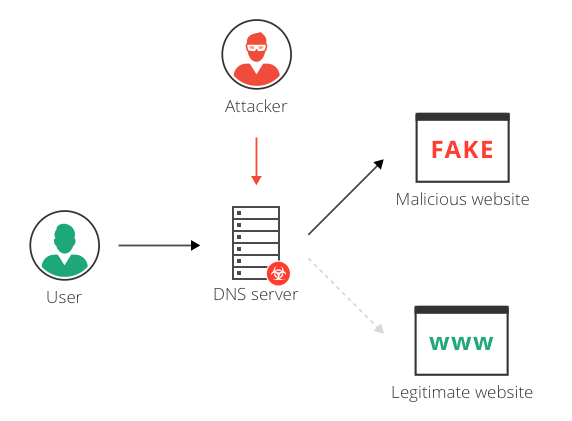 |
| User getting directed to malicious website with DNS cache poisoning - by Imperva |
Then how to avoid DNS cache poisoning?
It sounds such fetal attacks to be done to victims since if we're hooked into attack, we can easily give up our token, password to bank account and all the other valuable credentials.
But there is some tips to check if your're redirected to fake servers.
I especially want to emphasize this part since I was also once encountered with DNS spoofing attack and lost $100😂
🔒Always double-check your website
If you're feeling fishy about this directed website, you should check if the domain starts with HTTPS://~. I would not go on any website not enabling with TLS(Transport layer security). If it starts with HTTP://~, I highly recommend not to use their website thinking you've got redirected or their website is just fairly just shitty.
Check if there is HTTPS encryption
 |
| specifically SSL/TLS |
🔒Don't download suspicious files or download it through sandbox or virtual machine
This is fairly obvious. Downloading suspicious files not only lead to DNS cache poisoning but Trojan horse, exploit, XSS basically all types of malware

🔒Flush computer DNS cache as well as DNS cache stored in the router
Constantly checking your DNS cache and regularly flush your cache.
Checking your DNS cache - ipconfig/displaydns (window os)
Deleting all cache - ipconfig/flushdns(window os)
🔒Keep your anti-virus application up to date
Next post will be about DNS amplification
stay tuned



Comments
Post a Comment