[EN] Symmetric Algorithm - feistel vs SPN
☝Symmetric-Key Block Cipher
Designed to satisfy properties such as diffusion that hide the relationship between plaintext and ciphertext and confusions that hide the relationship between ciphertext and keys.
P-box(Permutation box)
1. Straight P-box : n=m
2. Expansion P-box : n<m
3.Compression P-box : n>m
(n-number of input bit // m-number of output bit)
(p-box is used for expansion of number of bits for many cases)
(no inverse function exists)
S-box(Substitution box)
n=m or n<>m(inverse function could be possibly existed or not)
1. shift
2. swap
3. split
4. combine
5. exclusive-OR
☝Product Cipher
Product cipher is combine of the components of a p-box and s-box in order to cover two properties(Diffusion + Confusion).
Product cipher is combine of the components of a p-box and s-box in order to cover two properties(Diffusion + Confusion).
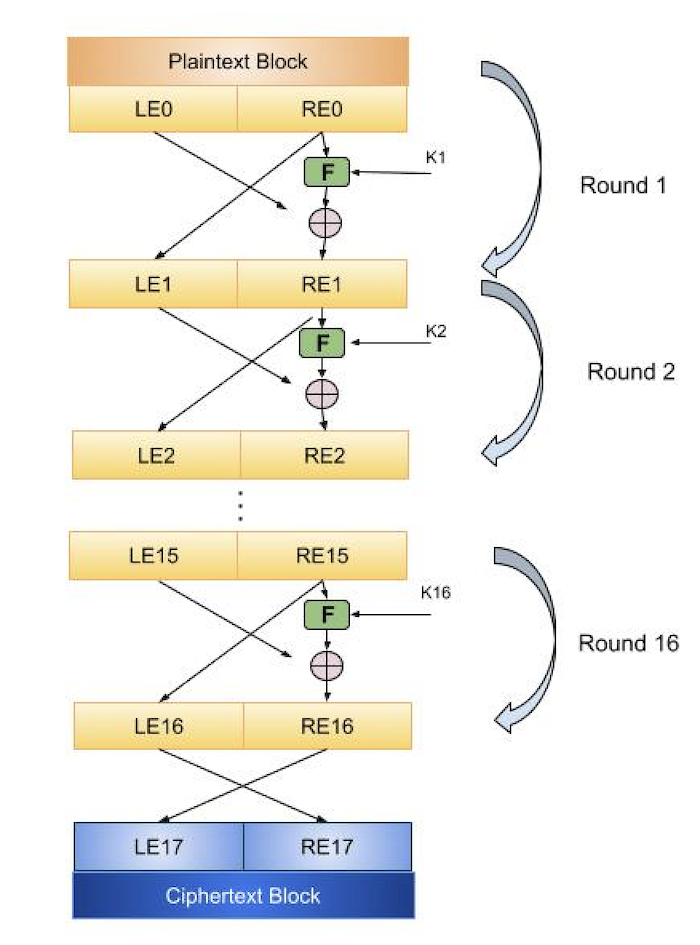
1. Feistel Cipher
There's two set : ant sets(working), grasshopper set(resting).
Only doing XOR and take it to swap is what grasshopper set is doing,
Taking half bits into Function and doing encryption is set ants.
BUT this set will be cross and sent it to next round.
Only doing XOR and take it to swap is what grasshopper set is doing,
Taking half bits into Function and doing encryption is set ants.
BUT this set will be cross and sent it to next round.
(process of Encryption = process of Decryption )
DES,SEED(korean encryption standard)
ROUND>=3 + even number
DES,SEED(korean encryption standard)
ROUND>=3 + even number
Considerations for implementing symmetric block passwords
Block size : more than 128bit
Key size : 128bit
number of rounds : more than 16
Subkey Generation Algorithm
Round Function
Key size : 128bit
number of rounds : more than 16
Subkey Generation Algorithm
Round Function
2. SPN NETWORK
(Substitution-Permutation Network)
After dividing the input value into blocks + processing the S-box.
After dividing the input value into blocks + processing the S-box.
Take it to permutation(p-box) process with processed S-box.(process of Encryption = process of Decryption )
AES,ARIA
*available for Parallel processing
AES,ARIA
*available for Parallel processing

💁Possible attack for Block Cipher
1. differential Cryptanalysis
This type of attack comes from the idea which is how could CipherText would be distinguished if you changed a part of the PlainText "CPA ATTACK"
CPA = chosen plaintext attack
2. Linear Cryptanalysis
Investigate the probability that several revisions of the plaintext and ciphertext bits of result which is zero, after XOR progress (Masui) "KPA ATTACK"
KPA = known plaintext attack
After XOR process, probability for 0 will be 1/2
Investigating bits which is not in this 1/2 probability can help to get information about key.
Which means
For linear detoxification, if you have found an approximate linear relationship,
This allows the transition from KPA to CPA.
This allows the transition from KPA to CPA.
3. exhaustive key search
4. statistical analysis
5. mathematical analysis
Stream Cipher
1. Synchronized stream cipher
The key stream is independent of the plain text or cipher text.
Plaintext or ciphertext between key bits are irrelevant at all
Plaintext or ciphertext between key bits are irrelevant at all
ex)
👀 OTP(one time pad)
Mathematically proofed that it is impossible to decipher by Shannon.
Literally a single-use pad, and every time you do an encoding, you're going to be able to create a random keystroke.
Unconditionally safe and theoretically unreadable.
Cryptographic and Decryption algorithms use Expensive ORs (reversely related to each other).
Literally a single-use pad, and every time you do an encoding, you're going to be able to create a random keystroke.
Unconditionally safe and theoretically unreadable.
Cryptographic and Decryption algorithms use Expensive ORs (reversely related to each other).
👀FSR(Feedback Shift Register)
👀LFSR(Linear Feedback Shift Register)
👀NLFSR(Non-Linear Feedback Shift Register)
2. Asynchronized stream cipher
The key stream is dependent on the plaintext or ciphertext.
This one method used to create different operating modes in block cipher which is
cipher feedback mode (CFB), actually generates stream passwords.
This one method used to create different operating modes in block cipher which is
cipher feedback mode (CFB), actually generates stream passwords.
1. No repeatable value inside the keystream value for a long period of time (pseudorandom)
2. Key stream is not linearly related to key. >(Finding the key stream value does not mean knowing the key value)
✊Considering the design of Stream Cipher
1. The continuation of Encryption should have a long cycle.
The pseudo-random number generator will eventually use a function that produces a bit stream that is repeated one day.
The longer iteration cycles mean that deciphering the code is as difficult.
2. Key stream is as similar as pseudo-random numbers.
3. You must be long enough to respond to an enterprise-wide attack.
Comments
Post a Comment